Humanity Protocol (H): Building trust in the world of AI
Identity confirmation has become one of the most problematic issues in the digital world. As artificial intelligence (AI) marches on, the line between real and bogus has blurred across social media, finance, gaming and other Web 2.0 and web3 platforms. The problem isn’t just limited to deepfakes or bots impersonating humans — it also includes individuals creating multiple fake accounts to manipulate systems, spread misinformation or exploit financial incentives. Existing identity solutions often depend upon centralized authorities that store and control user data, creating risks of surveillance, censorship and breaches.
Few projects have attempted to tackle these issues coherently. Sam Altman–backed Worldcoin (WLD) is one prominent attempt to solve the problem through biometric iris scans to verify user identity. While it promises global coverage and ease of proof, it has also faced criticism for concentrating control, collecting sensitive data and potentially building new forms of centralized biometric registries.
Humanity Protocol (H) is a decentralized platform that takes a different approach. It combines palm recognition technology with privacy-enhancing cryptographic tools and decentralized infrastructure to ensure users retain ownership and control of their data — and proves that they’re real, unique humans without revealing their private information. Humanity Protocol spreads trust across a network of independent validators, aiming to preserve privacy and reduce the risks of data monopolies.
Key Takeaways:
Humanity Protocol (H) is a decentralized identity network that combines palm biometrics, ZK proofs and blockchain validation to confirm real, unique human user identities while preserving their privacy.
The platform's native token, H, is used for staking, governance and for paying transaction fees when using the protocol's services.
H can be bought on Bybit as a USDT Spot pair or as a USDT Perpetual contract.
What is Humanity Protocol?
Humanity Protocol (H) is a decentralized identity network built on zkEVM Layer 2 blockchain technology that aims to provide a secure, privacy-preserving way to verify that each digital user is a real, unique human. The protocol combines biometric palm recognition, zero-knowledge (ZK) cryptography and a distributed network of validators to deliver proofs of humanity without relying on centralized authorities.
The protocol's human verification system addresses fundamental issues in digital identity verification: fake accounts, bots, Sybil attackers and automated manipulation that have become more prevalent as AI is used more actively throughout the digital world. Instead of a centralized database that exposes users to surveillance or breaches, Humanity Protocol enables users to retain control of their biometric data through encryption and on-chain verification.
The protocol encrypts biometric palm scans locally and transforms them into ZK proofs that confirm user identities without exposing raw biometric data, creating a Self-Sovereign Identity (SSI) framework that allows users to exercise full control and privacy over their identities. These proofs are validated on-chain by network actors called Humanity zkProofers. This decentralized approach reduces risks of censorship, data monopolies and identity fraud.
Humanity Protocol was founded in 2023 in Hong Kong by Terence Kwok. Its combination of cryptography, biometric technology and decentralized validation is designed to serve a wide range of Web 2.0 and web3 applications requiring reliable confirmation of unique human status.
Proof of Humanity
Proof of Humanity (PoH) is the protocol’s primary identity verification system. Users scan their palms with specialized hardware that captures unique vein patterns and geometrical features. This biometric data is encrypted locally and used to generate ZK proofs confirming the user’s existence and uniqueness.
Validators on the network (zkProofers) verify these proofs on-chain to ensure that identities are genuine, and are not duplicated. This decentralized verification system prevents Sybil attacks, multi-account abuse and automated bots designed to exploit systems.
PoH has a broad range of potential use cases. Within decentralized finance (DeFi), it can protect governance and reward distribution by confirming “one-person, one-vote” or one-wallet restrictions. Social media platforms can reduce fake accounts and bot-driven misinformation campaigns. Gaming ecosystems may benefit by limiting multi-accounting and automated scripts. Additionally, it can ensure fair token airdrops, improve decentralized governance transparency and support marketplaces that require verified human participants.
The protocol’s privacy-preserving design ensures that these applications don’t compromise user control or expose biometric information to centralized entities.
Palm recognition technology
Humanity Protocol uses AI-powered palm recognition combined with proprietary hardware to capture high-resolution scans of palm vein patterns, and geometric features unique to each user. The technology is designed to be accessible and secure on modern devices, serving as the biometric data source for PoH.
The protocol’s rollout consists of two phases:
Phase 1 focuses on deploying palm scanning technology and developing the cryptographic infrastructure to generate ZK proofs.
Phase 2 plans to expand validator networks, increase scanning accessibility and integrate PoH into more decentralized applications (DApps) across finance, governance and social platforms.
This phased approach balances technical maturity with scalability and aims to create a reliable, privacy-respecting identity verification system that can function at scale.
How does Humanity Protocol work?
Humanity Protocol (H) is structured around a user-controlled process that verifies real, unique human identities through encrypted biometric proofs and decentralized validation. The system combines hardware-based biometric capture, ZK cryptography and a distributed validator network.
Each Humanity Protocol user’s journey begins by enrolling for Proof of Humanity. A user scans the palm of their hand using dedicated technology that captures vein patterns and geometrical structures. The scan is processed locally, producing encrypted biometric data that never leaves the user’s device in raw form. Instead, it’s converted into a ZK proof — a cryptographic method that confirms validity without revealing underlying data. The proof confirms the user is a real, unique human, and that the palm scan isn’t duplicated in the system.
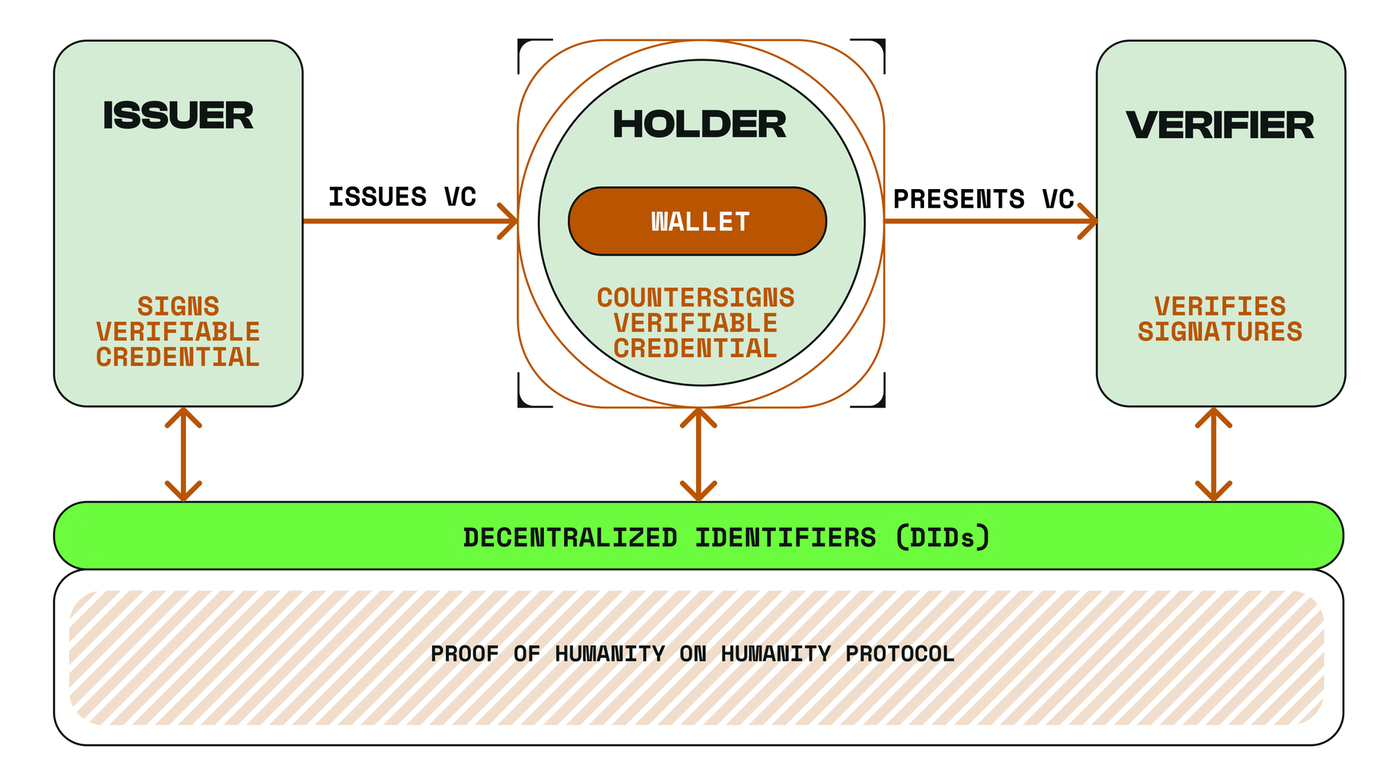
Once the proof is generated, it’s submitted to the network for validation. Here, the protocol relies on two key actors — Identity Validators (also known as Issuers) and Humanity zkProofers — to ensure decentralized, tamper-resistant confirmation of identity claims.
Identity Validators (Issuers) and Humanity zkProofers
Humanity Protocol operates within the Self-Sovereign Identity (SSI) framework. In this model, users retain control over their identity credentials, and decide how and where they’re used.
Identity Validators (Issuers) are trusted entities — potentially institutions, businesses or community organizations — that can attest to certain attributes of user identity within the Humanity Protocol ecosystem. Their role is to issue verifiable credentials (VCs) that confirm various details — such as age, citizenship, education, employment, achievements on various web3 platforms or other data — that’s relevant to third-party applications.
Alongside Issuers, Humanity zkProofers form the backbone of on-chain validation. zkProofers are independent network participants who confirm ZK proofs. They ensure each proof aligns with protocol requirements, that no duplication or tampering has occurred and that identity data remains private. Validators stake H tokens, and are economically incentivized to act honestly: malicious activity or inaccurate confirmations can result in slashing (punishing validators who act malevolently or irresponsibly) or removal from the network.
This dual-layer structure of Issuers and zkProofers ensures that Humanity’s system is resistant to centralized manipulation, while still supporting third-party attestations needed for use cases that require additional trust guarantees.
The Self-Sovereign Identity (SSI) framework
The SSI framework governs the way that identity data flows between users, Issuers and Humanity zkProofers. Users store their credentials locally or in personal wallets. They share only encrypted proofs with applications or services that request identity verification. Issuers verify specific claims, and zkProofers confirm the cryptographic integrity of ZK proofs. Together, these mechanisms maintain user control, data privacy and network integrity.
In practice, the protocol works like this: a user initiates a palm scan, then receives encrypted proof and (optionally) supplements that proof with credentials issued by Identity Validators, if a particular application requires them. zkProofers confirm the proof on-chain. The verified proof can then be used to access DeFi platforms, participate in governance, verify age for regulated services or prove uniqueness in social media environments.
This structure contrasts with traditional identity systems that depend upon centralized storage and constant third-party verification. Humanity Protocol distributes verification across network actors, removing reliance on a single authority and reducing the risks of data breaches or censorship.
The protocol is designed to scale by incentivizing new zkProofers and Issuers to join its network. As adoption grows, the validator set expands, further distributing trust and reducing the concentration of power. This decentralized approach aims to create a more resilient and censorship-resistant identity layer for digital platforms increasingly threatened by impersonators, bots and phony accounts.
Humanity Protocol key features
Human Recognition Module
The Human Recognition Module is the primary entry point for establishing an identity within Humanity Protocol. It combines purpose-built palm-scanning technology with AI algorithms that detect vein patterns and other unique palm features. This component is engineered for fast, secure operation: a user places their hand on the scanner, and within seconds the module captures and processes the scan data locally. The system has anti-spoofing properties to ensure the scan comes from a real human.
Critically, raw biometric data never leaves the user’s device. Instead, the module uses cryptographic techniques to transform the scan into a ZK proof, confirming the user is unique and real without revealing any underlying biometric details. This proof is then sent to Humanity Protocol’s network of validators, who check its validity and consistency with prior submissions. If the proof passes the necessary checks, it becomes part of the user’s verified identity record anchored on-chain, which applications can reference for access control, anti-Sybil measures and other services.
Verifiable credentials (VC)
VCs complement Humanity Protocol’s biometric layer by adding attestations from trusted third-party Issuers. These credentials can represent age verification, nationality confirmation, educational achievements, compliance with regulations or any other attribute tied to identity that applications might need to confirm. Humanity Protocol’s VC framework is built on open SSI standards, and places control of credentials fully in the hands of users, who store them in personal wallets.
When interacting with services, users decide which credentials to share. Third-party applications can verify the cryptographic signatures on the credentials without needing direct access to underlying personal data. This selective disclosure mechanism protects user privacy while enabling efficient verification. For example, a DeFi platform might require proof of jurisdiction or legal age, or a governance app could check community membership status. Issuers stake their reputations (and, potentially, H tokens) to ensure they only issue accurate credentials — since malicious or inaccurate issuance can lead to penalties and removal from the network.
The VC layer extends Humanity Protocol’s usefulness beyond basic verification of humanness, providing a flexible way to build richer identity frameworks needed for regulated environments, permissioned DeFi protocols, gated social communities and digital reputation systems.
Privacy-preserving data storage and use
Humanity Protocol is designed around decentralized, privacy-preserving data storage. Biometric scans never leave the local scanning device in raw form. Instead, ZK proofs and encrypted credential metadata are distributed using a decentralized peer-to-peer network that stores user data across independent nodes. References to this encrypted data are anchored on-chain, allowing validators and third-party applications to confirm authenticity without accessing or reading raw data.
Users hold the encryption keys to their own records and credentials. When verifying identity or credentials with external applications, they provide cryptographic proofs, instead of exposing any private details. This model dramatically reduces the vulnerability peculiar to centralized storage architectures, whereby large data silos can be targeted for breaches or exploited for surveillance. Humanity Protocol’s reliance on decentralized storage ensures data can’t be tampered with or censored, as encrypted records are spread across a global network of nodes.
What is the Humanity Protocol token (H)?
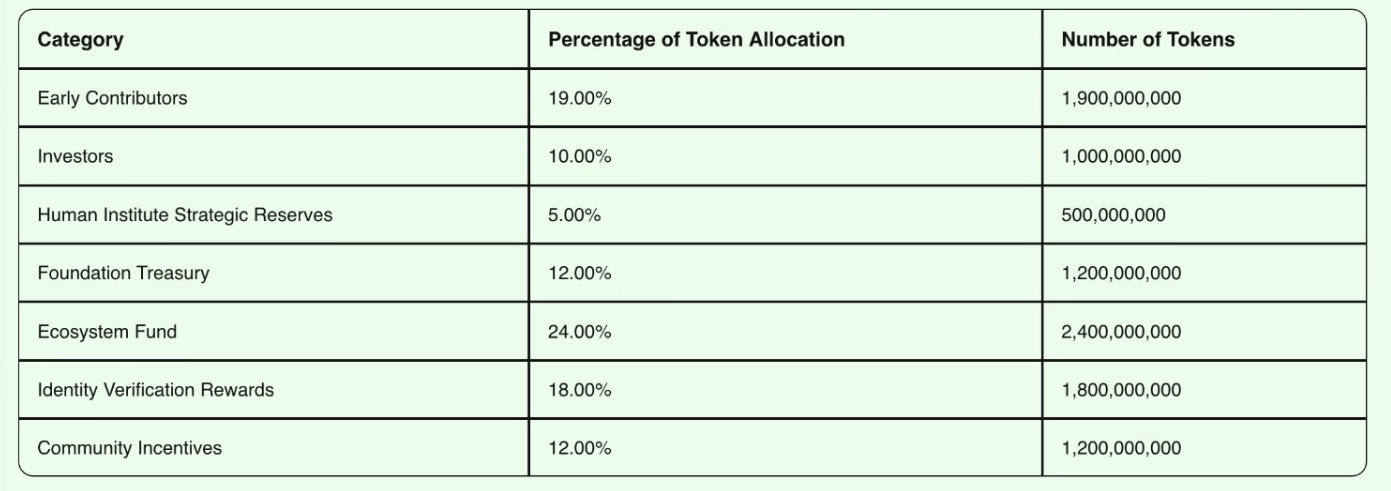
Humanity Protocol's native token, H, is an ERC-20 asset issued on the Ethereum (ETH) blockchain. It serves as the protocol’s utility and governance token, and is used for staking by zkProofers and Identity Validators, securing the protocol's consensus mechanism, paying network fees and participating in protocol governance decisions. All transactions on the protocol require payment using H tokens.
The H token has a total and maximum supply of 10 billion. Its supply allocations are per the image below:
Humanity Protocol token (H) airdrop controversy
Humanity Protocol launched H with a “fair drop” that required users to complete Human ID palm scans and participate in community and referral campaigns. The snapshot took place in June 2025, with the deadline for claims being June 24. Many protocol adopters who scanned their palms found themselves ineligible, or received little to no allocation, leading to backlash and accusations that the project had used individuals’ data to build hype while excluding genuine contributors. On the other hand, airdrop supporters argued that it was the first attempt at large-scale distribution tied to verified human uniqueness — and that no foul play was intended.
Where to buy the Humanity Protocol token (H)
The H token is available on Bybit as a Spot pair with USDT, and as a USDT-based perp contract. You can also take advantage of Bybit's event dedicated to the token to grab a share of the 9 million H prize pool:
New users can earn H tokens by accumulating a deposit volume of at least 2,000 H, or by depositing 100 USDT and trading 100 USDT worth of H via their first trade with Bybit.
Existing users can also earn rewards by trading at least 500 USDT worth of H on Bybit’s Spot market.
This event is valid through Jul 8, 2025, 10AM UTC.
Closing thoughts
By leveraging palm recognition technology, the Humanity Protocol team has developed a unique identification system that doesn’t expose personal data during the verification process. This is, however, not simply another biometric verification platform. Using blockchain technology, ZK proofs, encrypted decentralized storage and an established network of VC Issuers, Humanity Protocol’s identity model sails alone in a sea of biometric identity solutions that can't offer the same levels of security, immutability and privacy.
#LearnWithBybit